Phishing
What is Phishing?
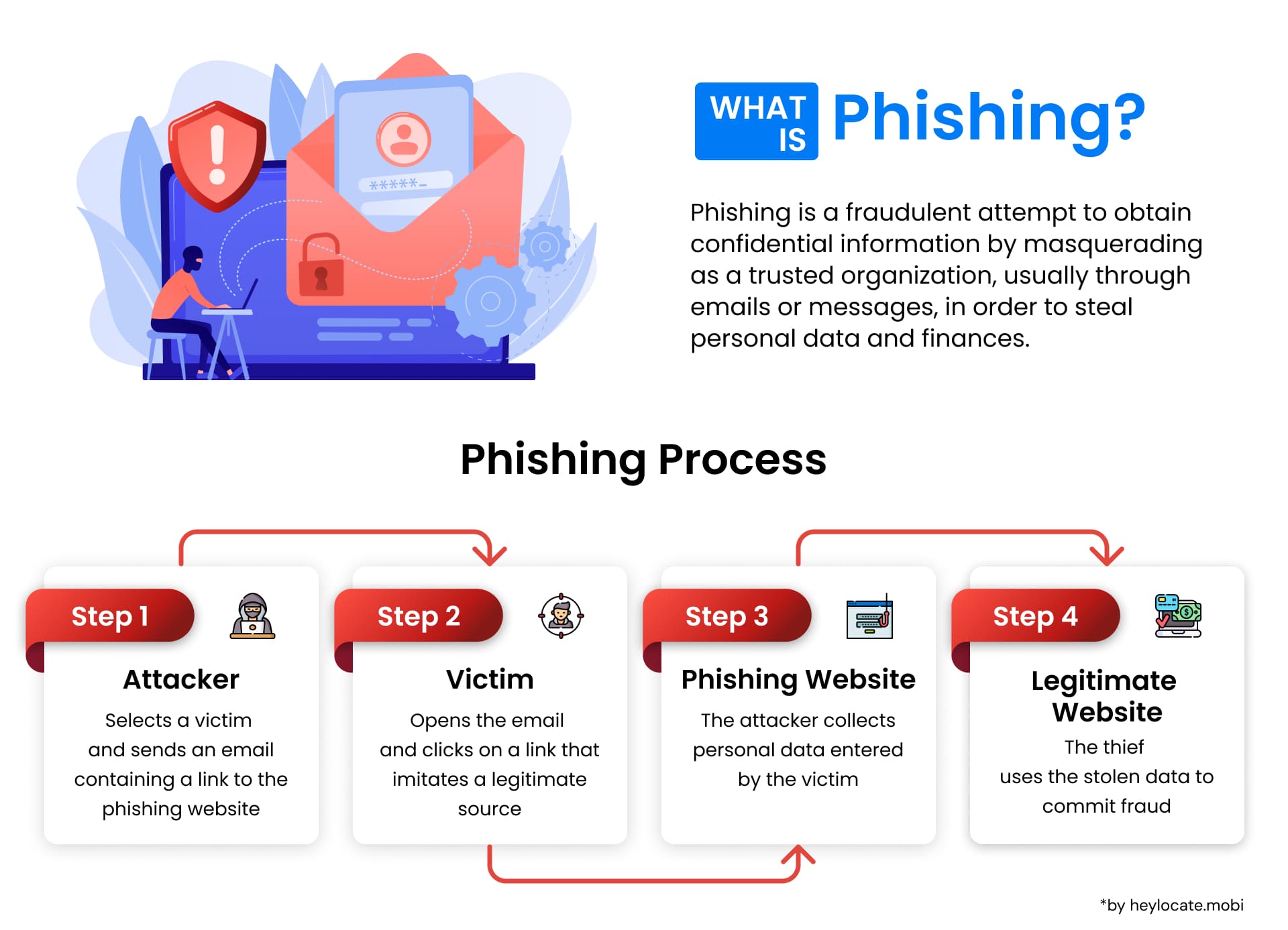
Phishing is a deceptive tactic employed by cybercriminals to dupe individuals into divulging sensitive information, encompassing passwords, credit card particulars, and social security numbers, among others. This tactic exploits human psychology and reliance on trust. Formally speaking, phishing can be defined as the fraudulent maneuver aimed at acquiring sensitive data by impersonating a reputable or trusted entity across electronic communication platforms.
Diverse Methods of Phishing
Phishing attacks come in various forms, each with its own unique characteristics and methods. Understanding these different methods can help individuals and organizations recognize and protect themselves against phishing attempts.
| Type of Phishing | Description |
|---|---|
| Email Phishing | One of the most widespread and impactful forms of phishing involves disseminating deceptive emails to a large audience, masquerading as reputable entities like financial institutions, social media platforms, or government bodies. |
| Spear Phishing | This is a highly focused form of phishing that zeroes in on particular individuals or organizations. Unlike run-of-the-mill phishing scams, spear phishing involves meticulous research and personalization to boost its success rate. |
| Whaling and CEO Fraud | This form of phishing sets its sights on high-ranking individuals within a company, such as executives or top management. One notorious type of whaling attack is CEO fraud, where scammers pose as a company’s CEO or other high-level executive, duping employees into transferring funds or revealing confidential information. |
| Clone Phishing | This scam involves making a duplicate of a genuine email and sending it to someone who’s already received the original. The copied email seems to come from a reliable source, like a familiar contact or service provider, but it has slight tweaks or updates. |
| Voice Phishing (Vishing) | Vishing employs voice calls to deceive individuals into divulging confidential information. These attacks may feature automated voice messages or live callers posing as trusted entities like financial institutions or government agencies. |
| SMS Phishing (Smishing) | This variant of phishing entails transmitting deceptive text messages to individuals. These messages frequently resemble authentic communication from reputable sources, urging recipients to act promptly or disclose sensitive data. |
| Page Hijacking | Browser hijacking is a tactic employed by scammers to covertly reroute users from secure websites to malicious ones. This method exploits vulnerabilities in web browsers, plugins, or website infrastructures. |
| Calendar Phishing | This is a recent form of phishing that exploits the calendar invitation feature in email clients. Scammers distribute false calendar invitations to people, frequently containing enticing offers or pressing requests. |
| Quishing (QR Code Phishing) | This is a method used by scammers to deceive individuals by misusing QR codes. They create counterfeit QR codes and disseminate them through various means, such as email, text messages, or physical stickers. |
Manipulative Tactics Employed in Phishing
Phishers utilize various manipulative strategies to deceive users and enhance the success of their attacks:
- Link Manipulation: Malicious links are disguised using URL shorteners or obfuscation techniques.
- Filter Evasion: Involves employing tactics such as misspelling words, using different character encodings, or embedding images with hidden text to bypass anti-phishing filters.
- Social Engineering: A psychological technique that exploits human trust and vulnerability by creating a sense of urgency, fear, or curiosity to prompt immediate action without careful consideration.
References
- Phishing – Wikipedia
- Phishing | What Is Phishing?
- What is a phishing attack? | Cloudflare
- What is a Phishing Attack? | IBM
- What Is Phishing? Examples and Phishing Quiz – Cisco
- What is Phishing? Definition, Types of Phishing, & Examples | Verizon
- Phishing attacks: defending your organisation | NCSC.GOV.UK – The National Cyber Security Centre