Two-Factor Authentication (2FA)
What is 2FA?
Two-Factor Authentication (2FA) is a security measure that adds another layer of protection to online accounts, enhancing security by requiring two different authentication factors for access.
Types of Authentication Factors
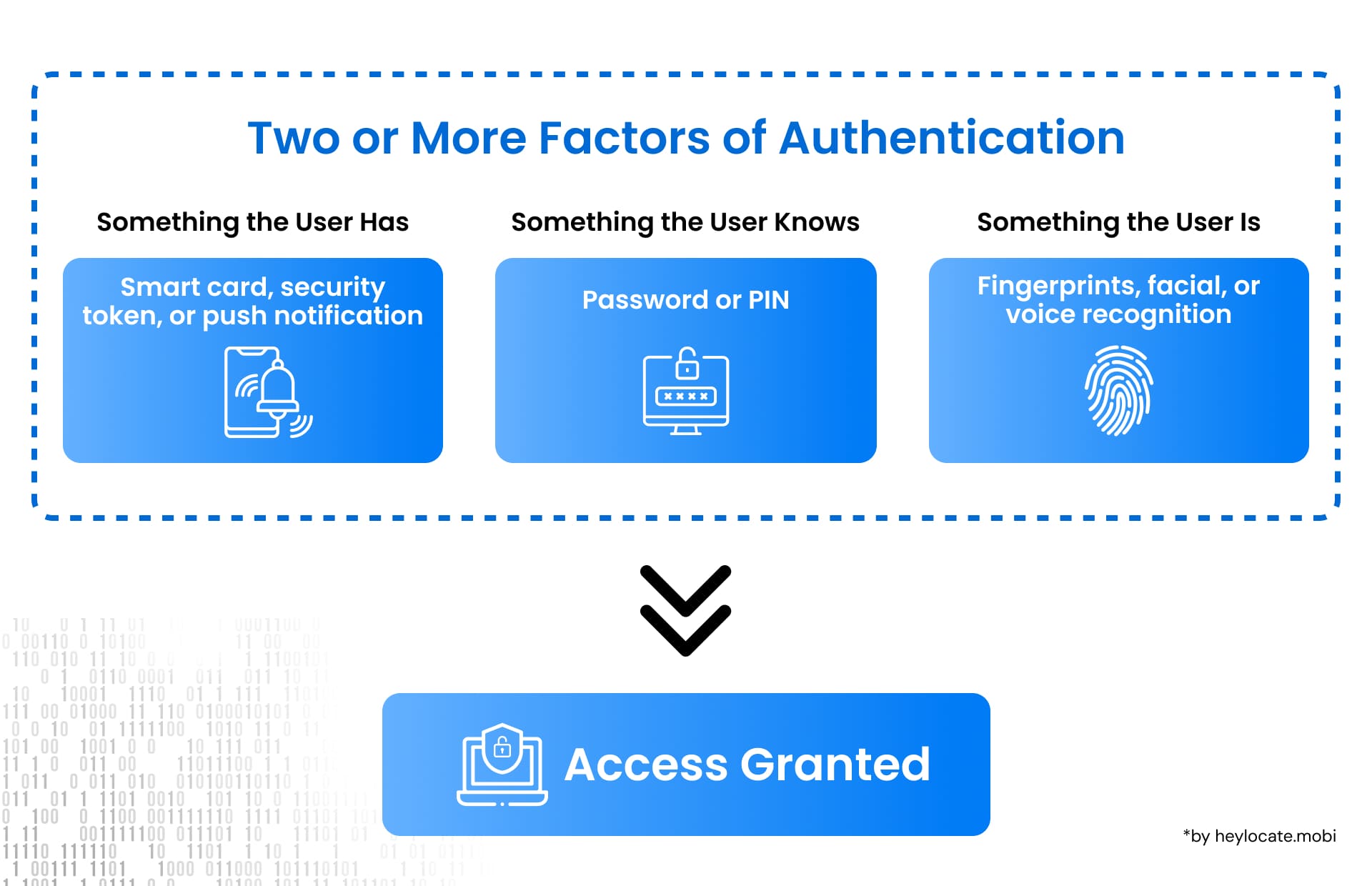
To understand 2FA, it is essential to explore the three main types of authentication factors:
- Something you have: This refers to any physical item possessed by the user, such as a special card, a security token, or a smartphone. These items generate unique codes required along with the password for access.
- Something you know: This authentication factor involves information known only to the user, like passwords, PINs, or secret phrases.
- Something you are: Biometric authentication relies on unique physical traits, such as fingerprints, facial features, eye patterns, or voice recognition.
Examples of Two-Factor Authentication
- ATM withdrawals: Requires both a bank card (possession) and a PIN (knowledge) for access.
- Online banking: Often employs 2FA by combining a username/password (knowledge) with an additional step, like entering a One-Time Password (OTP) sent to a mobile device (possession).
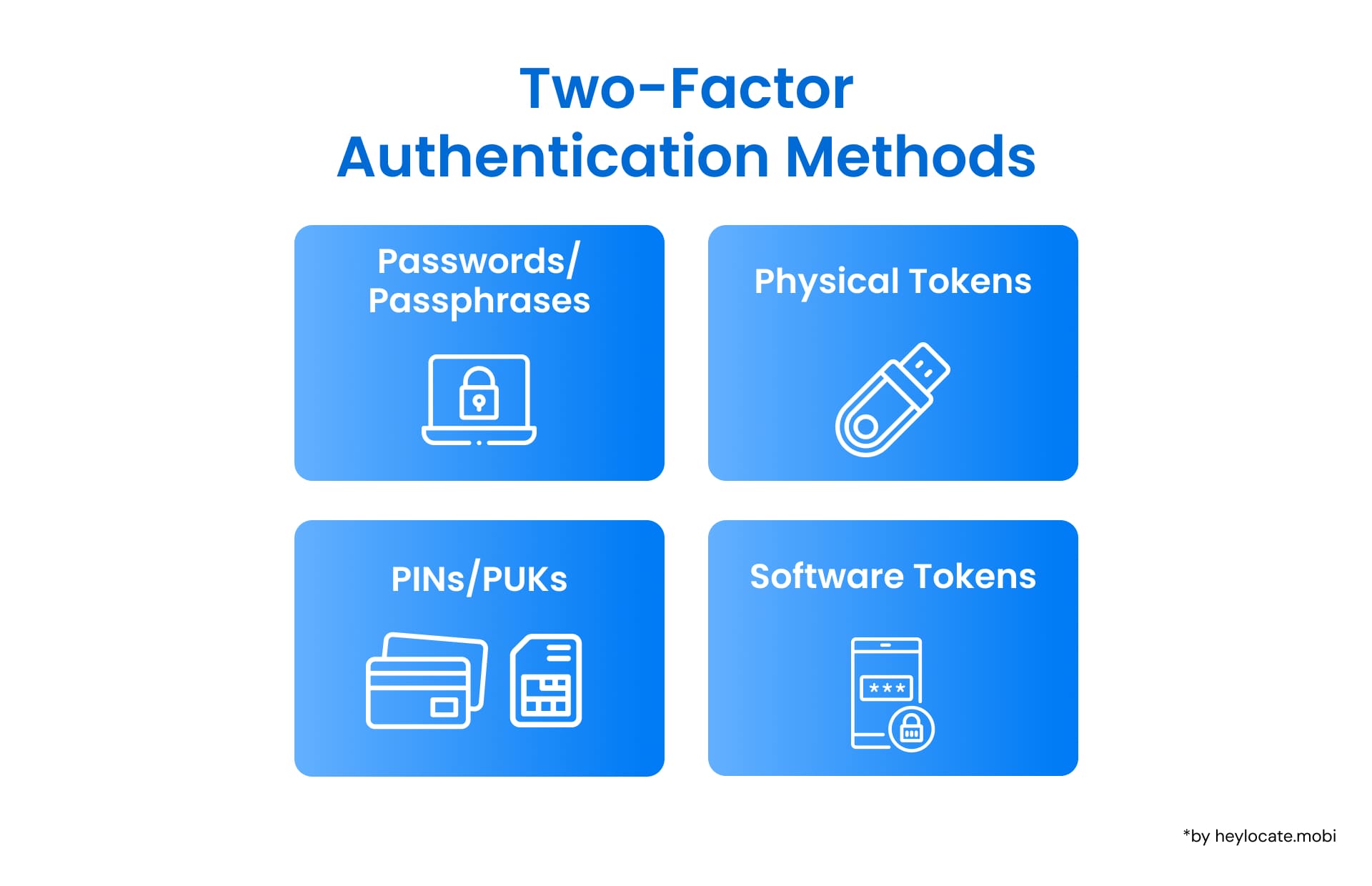
Passwords and Passphrases
These are combinations of characters used to secure online accounts. Strong passwords include a mix of uppercase and lowercase letters, numbers, and special characters. Passphrases, longer and easier to remember, provide robust security.
PINs and Other Secret Information
PINs are numeric codes used alongside physical cards or tokens for added security. Personal Unlocking Keys (PUKs) are utilized for unlocking SIM cards on mobile devices.
Physical Tokens
These tangible objects, like the RSA SecurID token, generate codes for authentication, enhancing security.
Software Tokens
Software tokens, like mobile apps generating One-Time Passwords (OTPs), provide 2FA without the need for physical devices.
Risks and Weaknesses
Although 2FA improves security, risks include social engineering attacks and interception of communication channels used for authentication.
Global Regulations
Authorities enforce Multi-Factor Authentication (MFA) to safeguard personal data, exemplified by regulations like the EU’s GDPR and the Payment Card Industry Data Security Standard (PCI DSS).
Implementation Challenges
Deploying MFA requires managing users, integrating with existing systems, and overcoming resistance through education and persuasion.
References
- Russell, S. (2023). “Bypassing Multi-Factor Authentication”. ITNOW, 65(1), 42–45.
- Jindal, S., & Misra, M. (2021). “Multi-factor Authentication Scheme Using Mobile App and Camera”.
- In G. S. Hura, A. K. Singh, & L. S. Hoe (Eds.), Advances in Communication and Computational Technology (pp. 787–813). Springer.
- “Two-factor authentication: What you need to know (FAQ)” – CNET. (2015). CNET. Retrieved October 31, 2015.
- Jacomme, C., & Kremer, S. (2021). “An Extensive Formal Analysis of Multi-factor Authentication Protocols”. ACM Transactions on Privacy and Security, 24(2), 1–34.
- Boeckl, K. (2016). “Back to basics: Multi-factor authentication (MFA)”. NIST. Retrieved April 6, 2021.
- Multi-factor authentication – Wikipedia.