Data Encryption
What is Data Encryption?
Data encryption is the conversion of readable data, termed plaintext, into an unintelligible form known as ciphertext. This transformation relies on encryption algorithms and keys, rendering the data indecipherable to unauthorized parties. Individuals possessing the appropriate decryption key can reverse the process, restoring the original plaintext. This ensures the security of the data, even in instances of interception.
Technical Foundations
At the heart of encryption lies the generation of pseudo-random encryption keys, which govern the transformation of plaintext into ciphertext through intricate mathematical operations executed by encryption algorithms. Decryption, in turn, entails reversing this encryption process using the identical key.
However, unauthorized decryption poses significant computational challenges, demanding substantial resources to breach well-designed encryption schemes within a feasible timeframe. Consequently, as computing capabilities progress, encryption algorithms must continually advance to thwart progressively sophisticated attacks.
Modern Encryption Standards
As computers became prevalent, encryption evolved from mechanical devices to computer algorithms, yielding two prominent types:
- Symmetric-key encryption: This method employs a single key for encryption and decryption processes, optimizing efficiency, especially for handling large volumes of data.
- Public-key encryption: Here, a key pair is utilized — a public key for encryption and a private key for decryption. This dual-key system enables secure communication without necessitating pre-shared secrets.
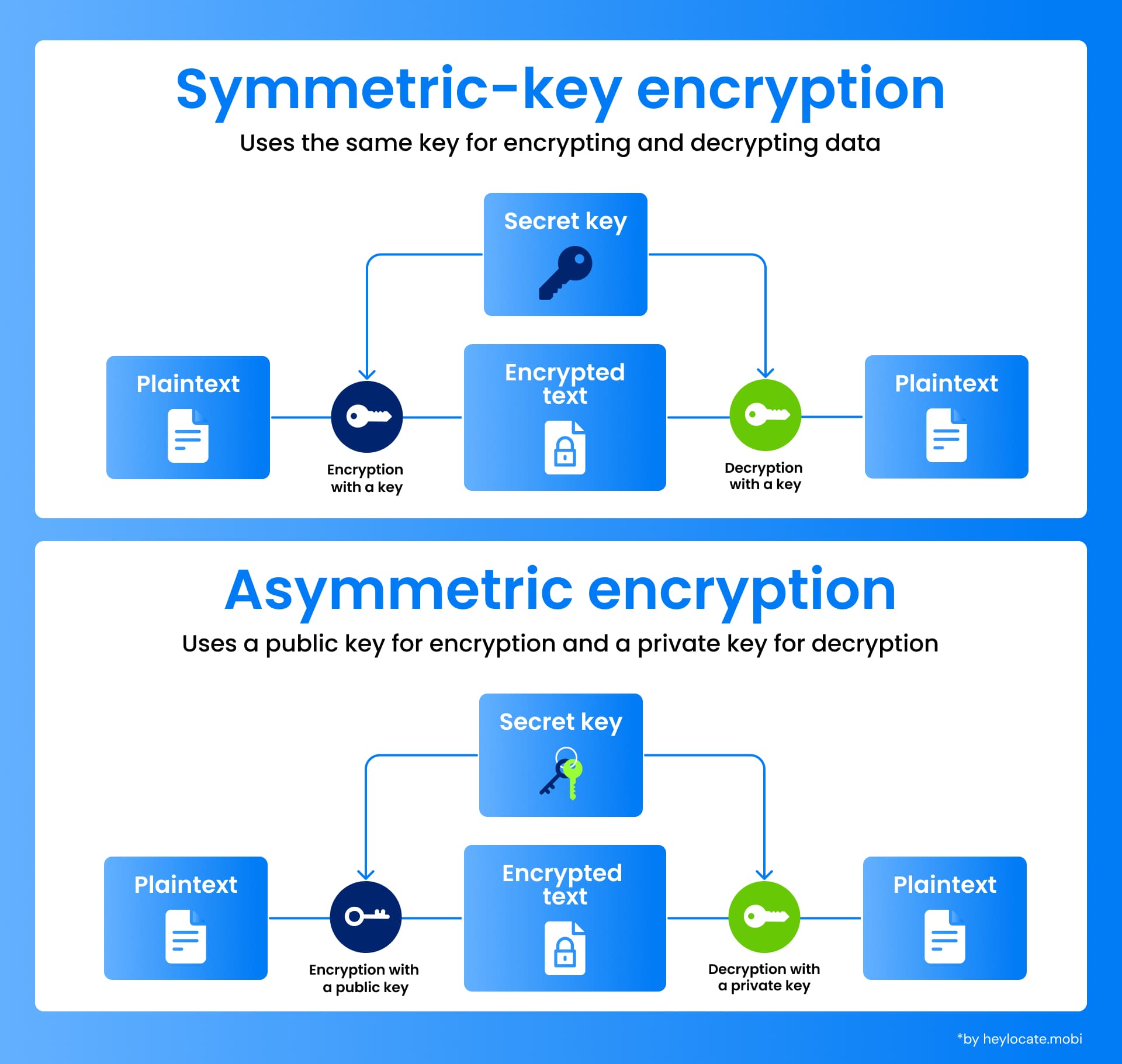
While modern encryption techniques are highly effective, ensuring robust data security necessitates meticulous key management and secure implementation practices.
Types of Encryption and Their Applications
As previously noted, Symmetric-key encryption relies on a shared secret key for both encryption and decryption, making it efficient for securing data at rest, such as databases or stored files. It finds suitability in scenarios where the same key can be securely exchanged between the sender and receiver.
In contrast, public-key encryption utilizes a pair of mathematically related keys: public and private keys. The public key, widely distributed, allows anyone to encrypt messages intended for the owner of the corresponding private key, which remains secret and is used to decrypt the encrypted messages.
Public-key encryption is commonly employed for secure communication across untrusted networks like the Internet. It facilitates the secure exchange of sensitive information without needing a pre-shared secret key. This encryption form plays a pivotal role in digital communication, enabling secure email, online banking, and other secure online transactions.
Applications of Encryption in Commercial and Civilian Context
Encryption is a cornerstone in numerous commercial and civilian domains, fulfilling critical functions across various applications.
In e-commerce, encryption is pivotal in safeguarding online transactions’ security and confidentiality. By encrypting sensitive data, such as credit card details, before transmission over the internet, encryption shields this information from potential interception by malicious entities, bolstering consumer trust and confidence in online shopping platforms.
Furthermore, encryption is extensively utilized in digital rights management (DRM), where content creators and distributors employ it to safeguard their intellectual property from unauthorized access or distribution. Through encryption, they can control who can access and utilize their digital content, safeguarding their proprietary rights and revenue streams.
Moreover, encryption is indispensable in facilitating secure communication channels, whether it entails exchanging sensitive information within organizational frameworks or transmitting confidential messages between individuals. By leveraging encryption, data confidentiality is upheld, thwarting unauthorized interception or tampering by external parties, thereby preserving the integrity and privacy of communication channels.
References
- Kessler, Gary (November 17, 2006). “An Overview of Cryptography”. Princeton University.
- “History of Cryptography”. Binance Academy.
- Unisys, Dr Glen E. Newton (2013-05-07). “The Evolution of Encryption”. Wired.
- “Key Cryptography – an overview | ScienceDirect Topics”. www.sciencedirect.com.
- Encryption – Wikipedia
- Caesar cipher – Wikipedia
- Public-key cryptography – Wikipedia
- Symmetric-key algorithm – Wikipedia