Proxy Server
What is a Proxy Server?
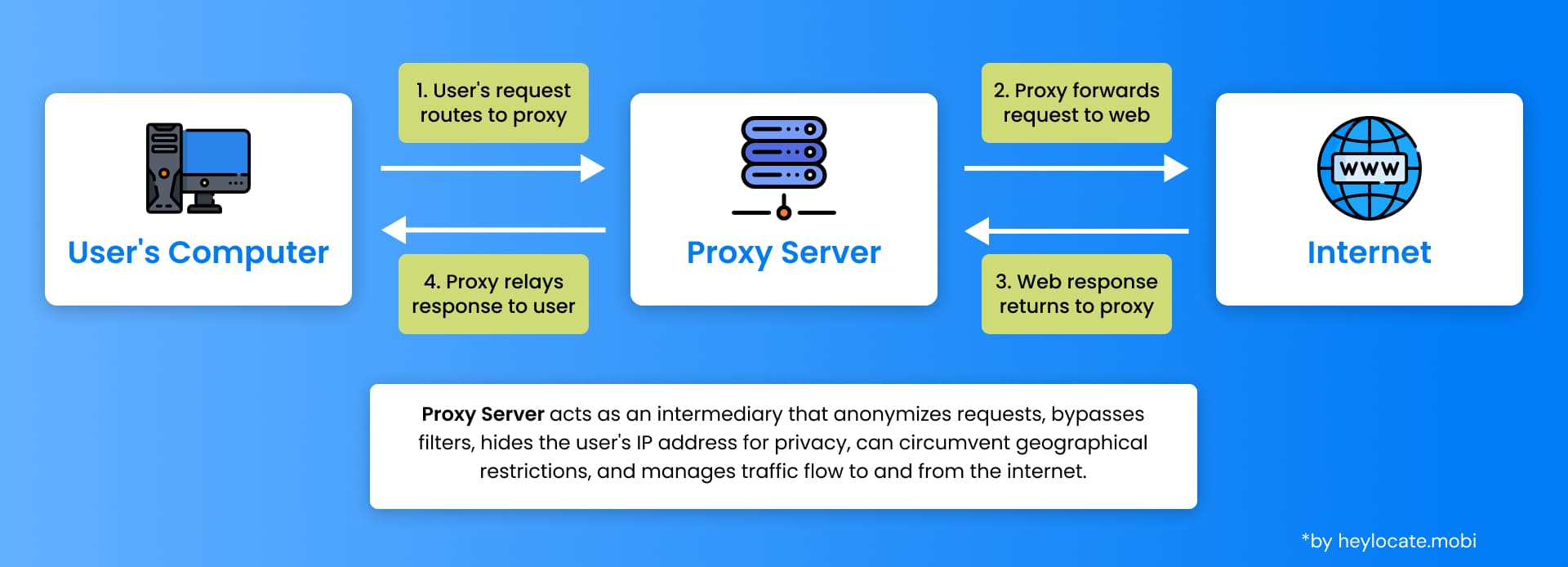
A Proxy Server is an intermediary application in computer networking that acts as a bridge between clients and servers. It receives requests from clients, such as web browsers, and forwards those requests to the appropriate servers. The server’s response is then sent back to the proxy server, which in turn relays it to the client. This process helps in enhancing privacy, security, and performance.
Various Types of Proxy Servers
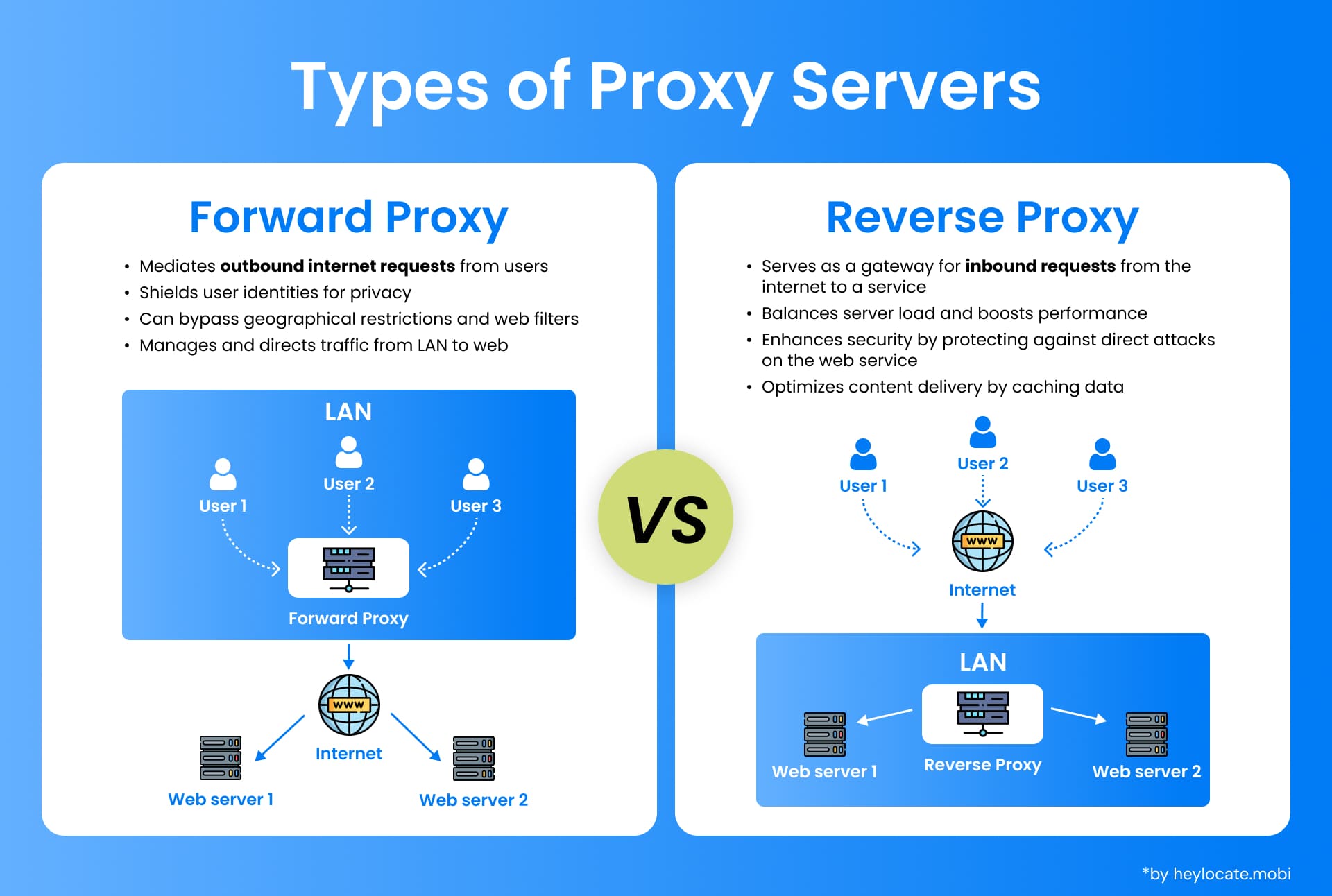
There are different types of proxy servers, each serving specific functions and use cases. Two primary classifications of proxy servers are forward proxies and reverse proxies:
- Forward Proxy (Regular Proxy)
The most common type. Intercepts client requests, forwards them to servers, retrieves responses, and sends them back to the client. - Reverse Proxy
It is located between the server and the client. Receives client requests, forwards them to servers, and delivers the server’s response to the client. Often used for security, load balancing, and performance enhancement.
Open Proxies and Their Classification
Open proxies are proxy servers that any internet user can access without authentication. They can be used to hide the client’s IP address, bypass content restrictions, or increase privacy. Open proxies can be further classified into anonymous and transparent proxies.
- Anonymous Proxies: These hide the client’s IP address from the server, making it difficult for the server to determine the client’s real location or identity.
- Transparent Proxies: These do not hide the client’s IP address and are often used for caching or content filtering purposes.
Specialized Proxies for Specific Functions
Beyond regular and reverse proxies, there are specialized proxies tailored to handle specific tasks. Let’s explore some examples like encryption/SSL acceleration proxies, load balancing proxies, caching proxies, and security proxies.
- Encryption/SSL Acceleration Proxies: These proxies pitch in by managing the SSL encryption process, taking the load off the server, and boosting overall system performance.
- Load Balancing Proxies: These proxies evenly distribute incoming client requests across multiple servers, ensuring each server can handle its share of the workload without getting overwhelmed.
- Caching Proxies: Think of these proxies as your personal librarian; they store copies of web pages, images, and other content to speed up retrieval when the same content is requested again.
- Security Proxies: These proxies act as your digital bodyguard, focusing on reinforcing security measures by filtering out harmful traffic and scanning for potential threats.
Risks of Open Proxies
While open proxies can provide anonymity and bypass content restrictions, they also expose users to potential risks. One major risk is the potential misuse of open proxies by malicious actors. Since open proxies are available to anyone, they can be abused for illegal activities, such as spreading malware, launching DDoS attacks, or engaging in cybercrime. Another risk is the potential leakage of sensitive information, as open proxies have access to the data being transmitted.
Reverse Proxies in Detail
Reverse proxies play a crucial role in enhancing security, load balancing, and performance in a network environment. They are positioned between the server and the client, acting as a gateway for incoming requests.
Applications and Advantages
| Applications | Advantages |
|---|---|
| Security | Act as a shield between server and internet, filter out malicious traffic, block potential threats, provide additional protection |
| Load Balancing | Distribute client requests across multiple servers, ensure even workload distribution, and prevent a single server from being overwhelmed |
| SSL Encryption / Decryption | Offload SSL processing from the server, improve server performance, and handle large SSL connections efficiently |
| Caching | Cache frequently accessed content, reduce server load, and improve overall performance |
References
- Proxy server – Wikipedia
- What is a Proxy Server? Definition, Uses & More | Fortinet
- What is a Proxy Server and How Does it Work? | Varonis
- What is Proxy Server? – GeeksforGeeks
- What is a Proxy Server? How They Work + Security Risks | UpGuard
- What is a Proxy Server? Definition, How It Works & More | Digital guardian