Cybersecurity
What is Cybersecurity?
Cybersecurity is the guardian of electronic data and systems, shielding them from unauthorized intrusions, data breaches, and cyber-attacks. It encompasses a variety of measures and techniques crafted to safeguard computer networks, devices, and information from internal and external threats.
Considering that businesses, governments, and individuals rely heavily on computers and the Internet, cybersecurity ensures data confidentiality, integrity, and availability. It plays a crucial role in safeguarding sensitive information such as personal data, financial transactions, and confidential documents. The repercussions of cybersecurity breaches can be severe, including financial loss, reputational damage, and legal implications.
The Necessity for Cybersecurity
The necessity for cybersecurity has surged exponentially due to the increasing dependence on computer systems, the internet, wireless network standards, and smart devices. With the emergence of the Internet of Things (IoT), the attack surface has widened, making it imperative to secure these interconnected devices. Furthermore, the complexity of information systems and the sophistication of cyber-attacks necessitate robust cybersecurity measures.
Understanding Vulnerabilities and Attacks
Vulnerabilities in computer systems and networks can arise from flaws in design, implementation, operation, or control. Cybercriminals exploit these vulnerabilities to gain unauthorized access or compromise the integrity of data.
- Design vulnerabilities: These weaknesses stem from the initial design of a system, making it susceptible to exploitation. Examples include improper access controls, weak encryption algorithms, or flawed authentication mechanisms.
- Implementation vulnerabilities: Arising during the development and deployment of a system, these vulnerabilities result from coding errors, misconfigurations, or inadequate testing.
- Operational vulnerabilities: Related to the day-to-day operation and maintenance of a system, these vulnerabilities can result from poor security practices such as weak passwords, lack of security updates, or failure to patch known vulnerabilities.
- Control vulnerabilities: These weaknesses pertain to administrative controls and policies governing system usage. They can be exploited through social engineering tactics or insider threats.
Common Cyberattacks
Cyberattacks manifest in various forms, each with its own goals and techniques.
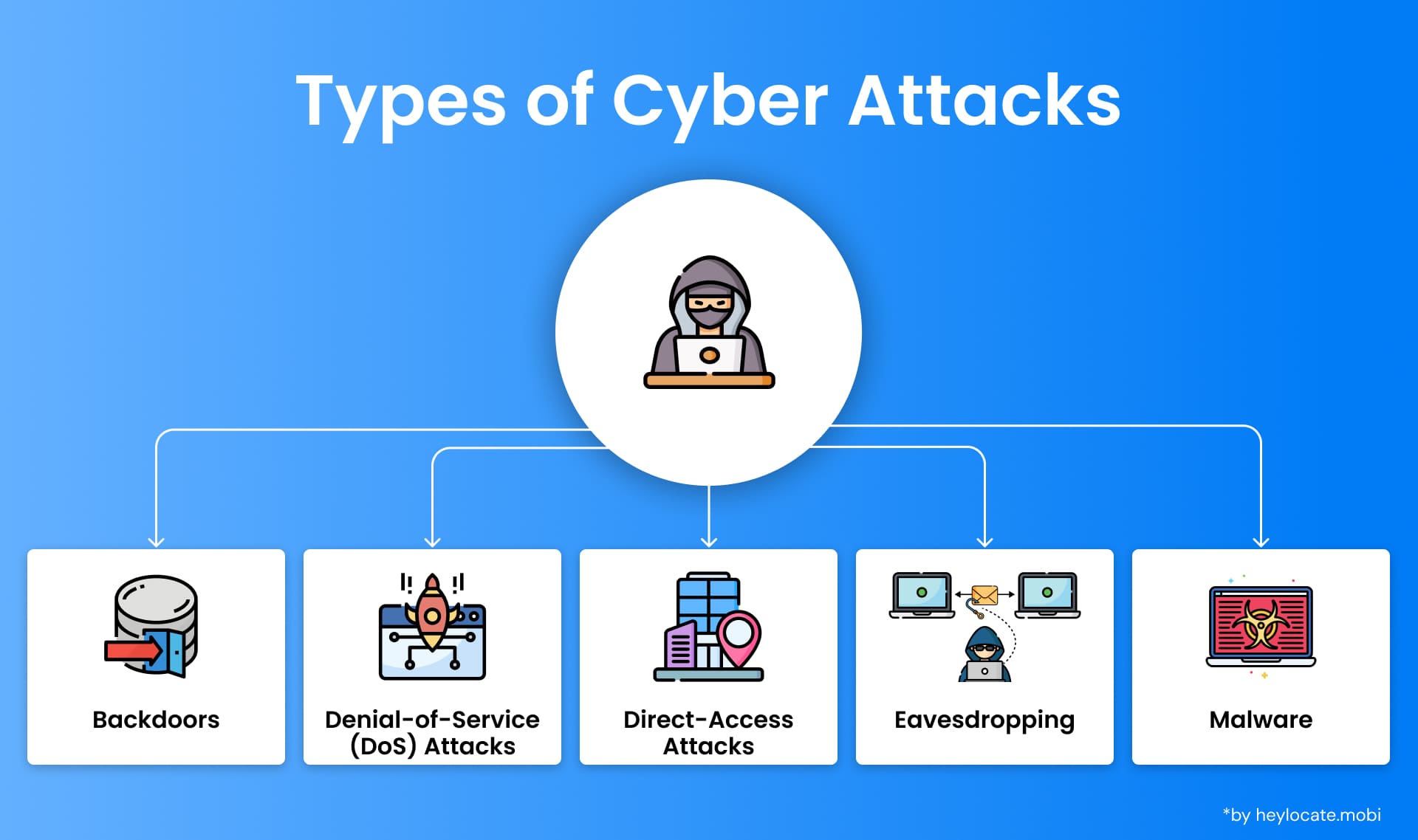
- Backdoors: These hidden entry points into a system allow unauthorized access, enabling cybercriminals to bypass authentication mechanisms.
- Denial-of-Service (DoS) Attacks: These attacks disrupt the availability of a computer system or network by overwhelming it with illegitimate requests or traffic.
- Direct-Access Attacks: Cybercriminals physically gain access to a system or network through theft, unauthorized entry, or hardware tampering.
- Eavesdropping: Involves the unauthorized monitoring or capturing of data transmitted over a network.
- Malware: Refers to software designed to harm or exploit computer systems or networks.
Implementing Cybersecurity Measures
To mitigate cyber threats, implementing effective cybersecurity measures is essential.
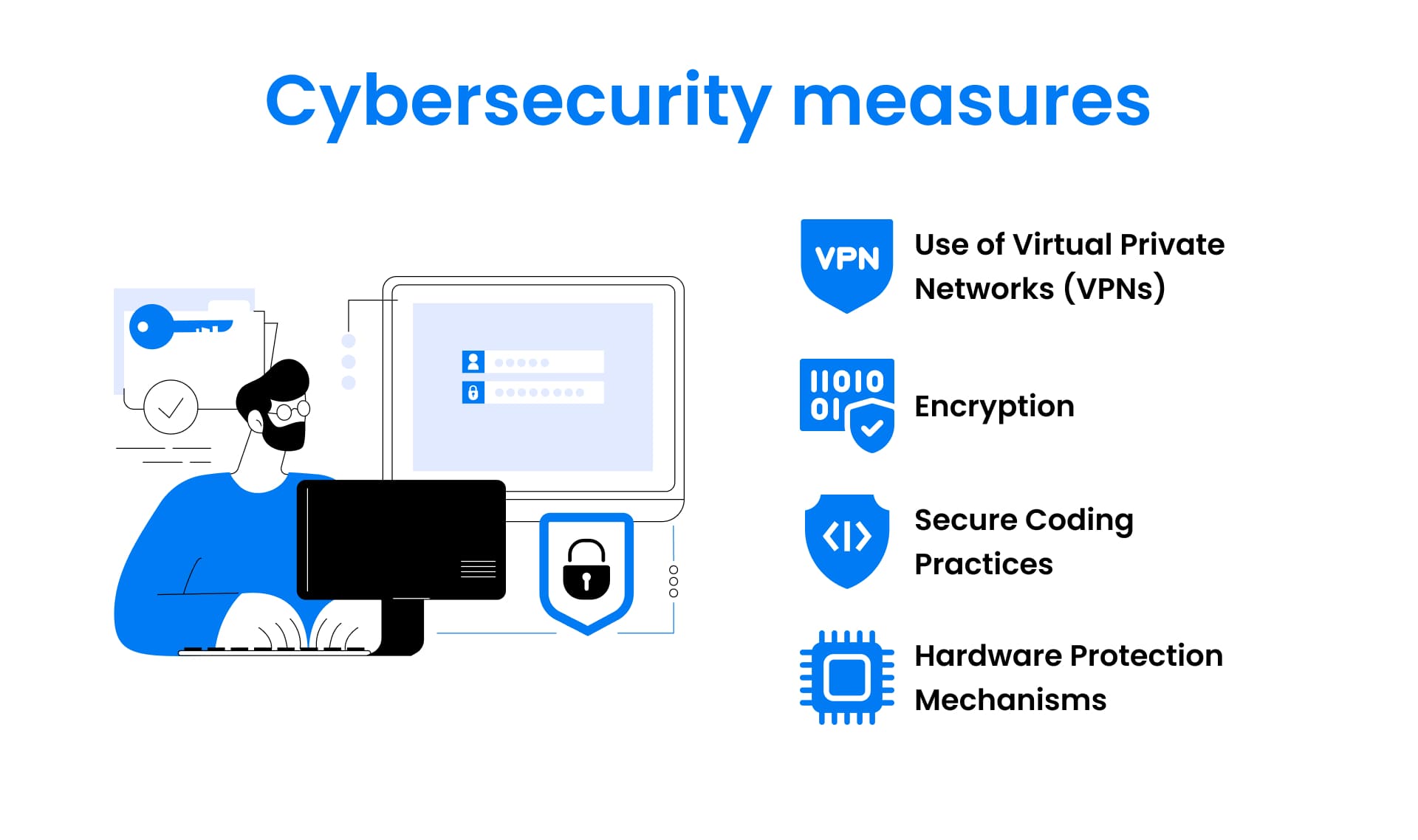
- Use of Virtual Private Networks (VPNs): Encrypts internet traffic to prevent interception by cybercriminals.
- Encryption: Converts data into an unreadable form using cryptographic algorithms to ensure confidentiality.
- Secure Coding Practices: Minimizes vulnerabilities by writing robust, secure code.
- Hardware Protection Mechanisms: Provide an additional layer of security to safeguard against tampering or unauthorized access.
Emerging Threats and Continuous Adaptation
Cybersecurity is dynamic, requiring continuous adaptation to emerging threats.
- Multi-vector attacks: Involve using multiple attack vectors simultaneously to target a system or network.
- Polymorphic attacks: Malware designed to change its form and behavior to evade detection constantly.
Practical Applications of Cybersecurity
Corporate and governmental cybersecurity practices involve technical controls, employee training, and incident response protocols.
Global Cybersecurity Efforts
International cooperation and collaborative efforts are vital to combat cybercrime and improve cybersecurity. Initiatives such as the Budapest Convention on Cybercrime and the Cybersecurity Framework by the National Institute of Standards and Technology (NIST) provide guidelines and frameworks for international cooperation and best practices.
References
- Schatz, Daniel; Bashroush, Rabih; Wall, Julie (2017). “Towards a More Representative Definition of Cyber Security”. Journal of Digital Forensics, Security and Law. 12 (2).
- Computer security at the Encyclopædia Britannica
- Stevens, Tim (11 June 2018). “Global Cybersecurity: New Directions in Theory and Methods” (PDF). Politics and Governance.
- Cybersecurity – Wikipedia
- Common Vulnerabilities and Exposures (CVE) – MITRE
- Budapest Convention on Cybercrime – Council of Europe
- Cybersecurity Framework – National Institute of Standards and Technology (NIST)