Virtual Private Network (VPN)
What is VPN?
A Virtual Private Network (VPN) is a secure connection method used to add privacy and security to private and public networks, such as the internet. VPNs create a secure tunnel between the user’s device and a remote server, allowing data to be transmitted securely over an existing network.
Technical Foundations of VPNs
VPNs rely on virtual point-to-point connections, which emulate a direct, physical link between the user’s device and the remote server. These connections are established using tunneling protocols, which encapsulate the user’s data within a secure “tunnel” that unauthorized individuals cannot intercept or access.
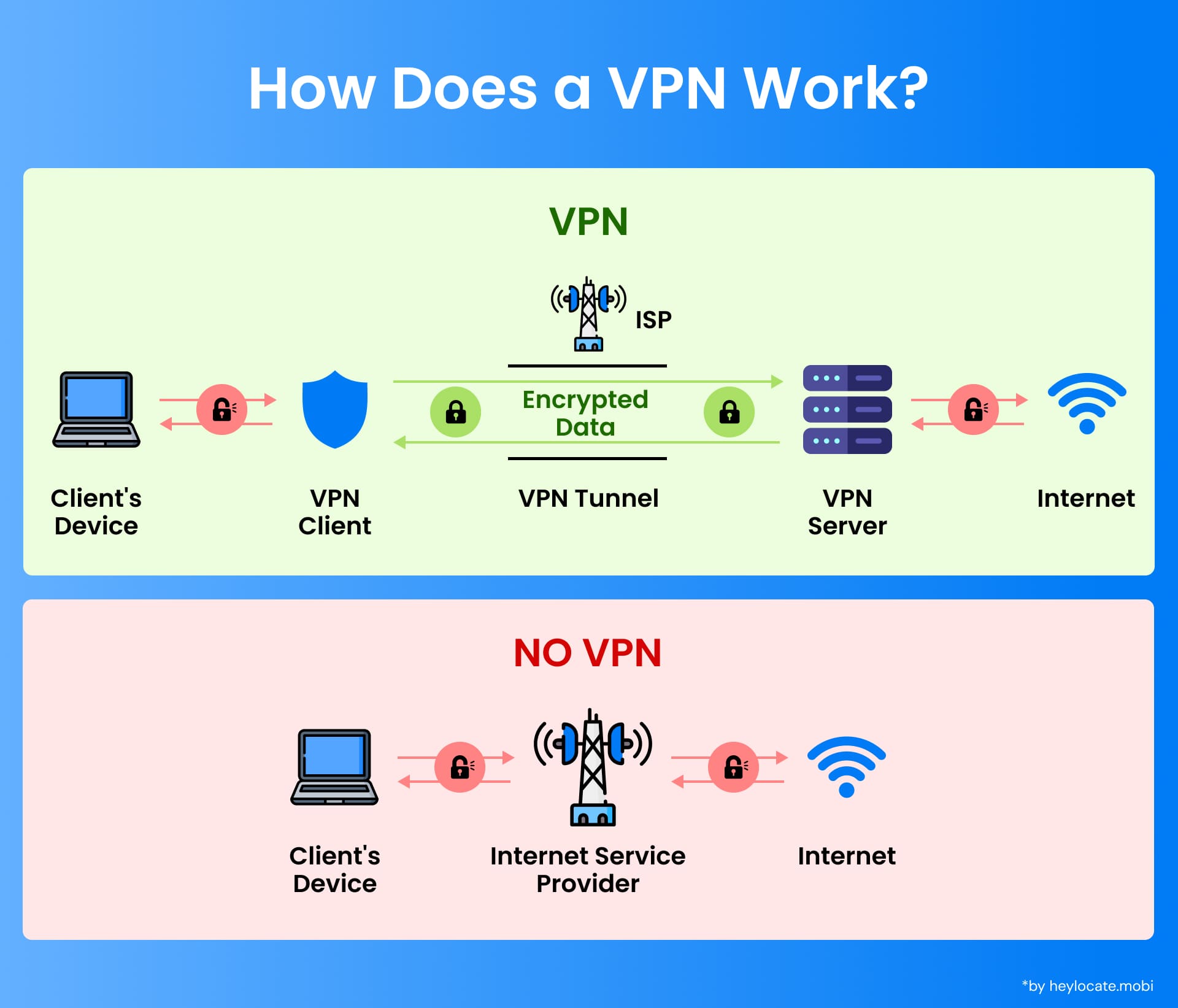
VPN Classifications
VPNs are categorized based on their connection type:
- Remote Access VPNs: Allow individual users to securely connect to a private network from remote locations.
- Site-to-Site VPNs: Establish secure connections between two physically separate networks, often used by businesses with multiple locations.
VPN Types and Their Applications
| VPN Type | Description | Application |
|---|---|---|
| Remote Access VPN | Enables individual users to connect to a private network from remote locations securely | • Secure remote work access to company resources (files, applications, databases) |
| Site-to-Site VPN | Establishes a secure connection between two physically separate networks | • Secure connections between branch offices or data centers for resource sharing and collaboration (common in businesses with multiple locations) |
| Extranet-Based VPN | Connects networks from different organizations | • Secure communication and data sharing between partner organizations in B2B scenarios • Secure connections between a cloud provider and a client’s network in cloud computing environments |
VPN Systems and Security Protocols
VPNs rely on various security protocols to ensure data confidentiality, integrity, and authenticity:
- Tunneling Protocols: Establish secure tunnels (IPsec, SSL/TLS, OpenVPN).
- Encryption: Protects data confidentiality by making it unreadable without a decryption key.
- Authentication: Verifies the identity of users and prevents unauthorized access (passwords, biometrics, two-factor authentication).
- Message Integrity Checks: Use message authentication codes (MACs) to detect data tampering during transmission.
VPN Security Model and Authentication
VPN security involves robust authentication mechanisms, including passwords, biometrics, and two-factor authentication. Message authentication codes (MACs) are used to ensure the security and integrity of data packets transmitted over the VPN.
Advanced VPN Features and Functionalities
- Provider-Provisioned VPN Components: Utilize dedicated components (Customer devices, CE devices, PE devices, and provider devices) to manage VPN connections.
- VLANs (Virtual Local Area Networks): Segment a physical network into virtual ones for enhanced security and isolation.
- VPLS (Virtual Private LAN Service): Emulates a LAN over a wide area network, allowing sites to communicate as if on the same physical network.
VPN Architectures and Technologies
- OSI Layer 2 VPNs: Operate at the data link layer, using protocols like MPLS and BGP for secure connections across networks (maintains same IP addressing across sites).
- OSI Layer 3 VPNs: Operate at the network layer, using IP routing protocols like BGP for secure connections (allows separate IP addressing schemes across sites).
- Unencrypted Tunnels: Offer increased performance but lack encryption security.
- Trusted Delivery Networks (MPLS): Provide secure and reliable transport for VPN traffic.
VPNs in Mobile Environments
- Mobile VPNs: Enable secure access to enterprise resources from mobile devices on public Wi-Fi networks.
- Challenges: Network connectivity issues, maintaining secure sessions.
- Solutions: Automatic reconnection, seamless handover, adaptive encryption.
Networking Limitations and Advanced Solutions
- Limitation: Inability to support broadcast domains (traditional network communication method).
- Solutions: VPLS and Layer 2 Tunneling Protocols (L2TP, PPTP) allow broadcast message transmission over VPNs.
References
- Wikipedia: Virtual_private_network
- What is a VPN, Kaspersky.com
- What is VPN, Microsoft.com, Computing Dictionary
- What is VPN, Cisco.com
- What is a VPN, nordvpn.com
- What is a VPN and Why You Need One, PCmag
- VPN, Proofpoint.com