End-to-End Encryption
What is End-to-End Encryption?
End-to-End Encryption (E2EE) is a communication protocol ensuring only authorized parties can access transmitted messages. Its primary objective is to safeguard against unauthorized access and tampering of data.
How it Works
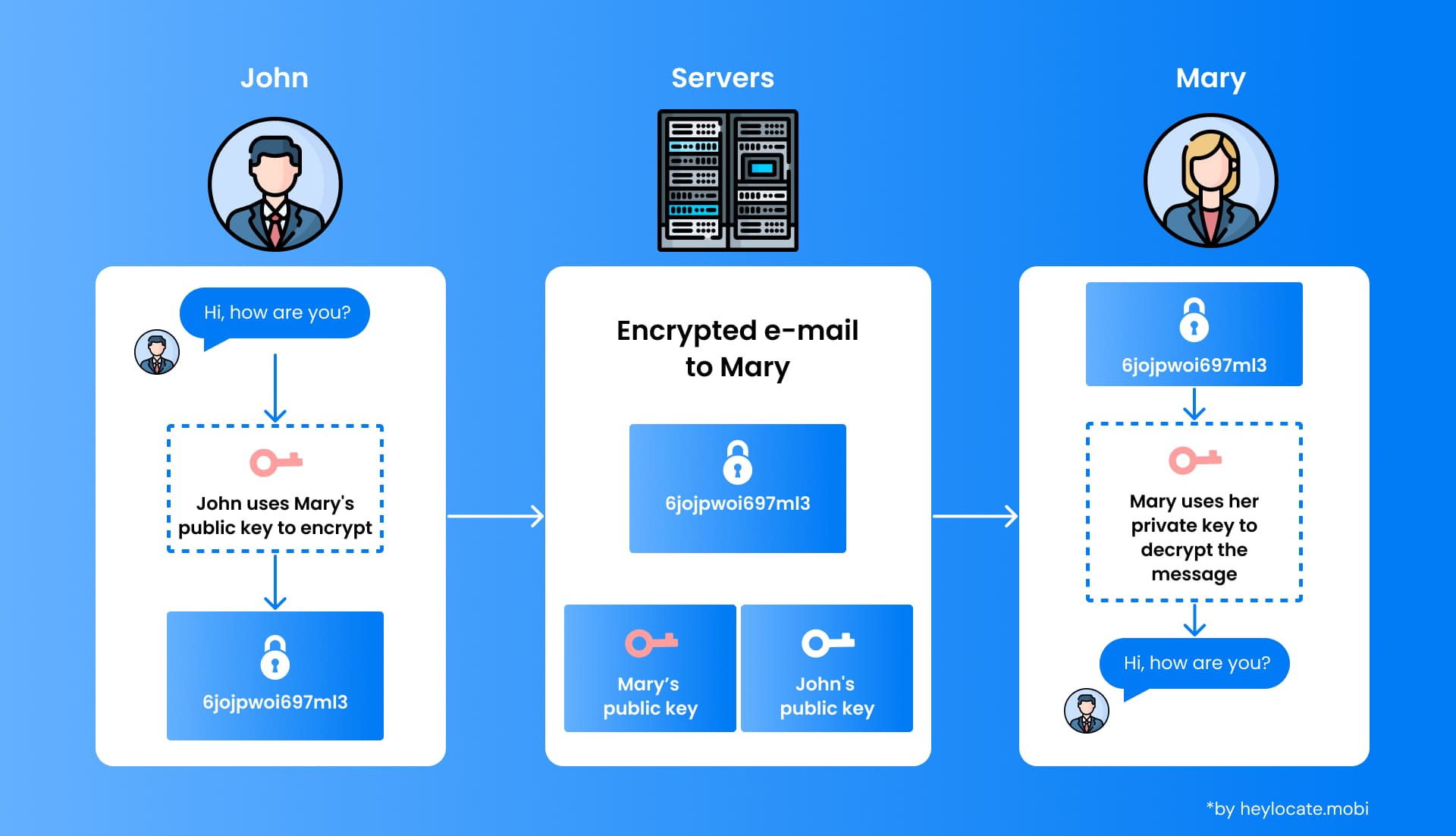
E2EE operates by encrypting data at the sender’s device and decrypting it at the recipient’s end. Encryption involves transforming plain text into ciphertext using unique keys. This ciphertext can only be deciphered using the corresponding decryption key. E2EE operates without intermediary servers, ensuring message security even if the server storing encrypted data is compromised. It utilizes strong encryption algorithms and secure key exchange protocols.
Importance of End-to-End Encryption
End-to-End Encryption (E2EE) stands as a cornerstone in contemporary digital communication systems, offering myriad privacy and security advantages. Foremost among these benefits is its safeguarding of user privacy, ensuring that only the communicating parties possess access to message content. Unlike conventional communication setups where service providers might potentially access and scrutinize message contents, E2EE averts such unauthorized intrusions.
By encrypting data at the sender’s end and decrypting it solely at the recipient’s device, E2EE guarantees the confidentiality of message contents. This proves particularly pivotal in scenarios necessitating the secure exchange of sensitive information, such as personal conversations, financial particulars, or proprietary data. E2EE systems furnish a level of privacy unattainable through traditional communication avenues.
Moreover, E2EE serves as a bulwark against interception and tampering by malicious entities. Even in the event of encrypted data interception, E2EE renders the contents indecipherable to unauthorized parties lacking the encryption key. Consequently, hackers encounter significant hurdles in gaining illicit access to sensitive information, thereby mitigating the risks of data breaches and unauthorized disclosures.
Limitations
One of End-to-End Encryption (E2EE) limitations is its inability to ensure absolute confidentiality and security. While the encryption and decryption processes themselves are robust, attackers may exploit weaknesses at the communication endpoints, compromising device security rather than directly targeting the encryption algorithm or key exchange mechanism.
Another significant challenge is posed by the threat of man-in-the-middle (MITM) attacks. In such attacks, an adversary intercepts communication between two parties and masquerades as each party to the other, effectively eavesdropping on the conversation.
E2EE alone is insufficient to thwart MITM attacks, as attackers can intercept encryption keys and decrypt messages before re-encrypting them with their own keys. Additional authentication measures are imperative to mitigate the risk of MITM attacks effectively.
Current State of E2EE in Digital Communication
Numerous messaging platforms, such as WhatsApp, Signal, and Telegram, have embraced End-to-End Encryption (E2EE). Thus, these platforms guarantee that all messages, voice calls, and video calls are encrypted end-to-end, affording users heightened privacy and security.
Nevertheless, not all messaging applications incorporate E2EE as a default feature. Some platforms, including Facebook Messenger and Google Hangouts, rely on server-based encryption, wherein messages are encrypted during transit between the sender and the server but can be decrypted and accessed by service providers. This raises apprehensions regarding the privacy and security of messages, as they remain susceptible to unauthorized access by service providers or third parties.
Challenges in Implementing E2EE
In implementing End-to-End Encryption (E2EE), authentication plays a pivotal role in mitigating the risk of man-in-the-middle (MITM) attacks. In an MITM attack, an intruder intercepts communication between two parties and masquerades as each party to the other, clandestinely eavesdropping on the conversation. Attackers can intercept encryption keys and decrypt messages before re-encrypting them with their own keys.
Thus, E2EE systems employ various authentication methods, such as digital certificates, where each user possesses a unique digital certificate that verifies their identity.
PKI (Public Key Infrastructure)
PKI involves the use of public keys, which can only be decrypted by the corresponding private keys. PKI supports various applications such as secure email and web browsing.
PSK (Pre-Shared Keys)
PSK authentication relies on the sharing of a secret key between parties before communication begins. It is simpler to implement but requires careful management of shared keys, usually used in VPNs, Wi-Fi networks, and small-scale IoT deployments.
Endpoint security
The endpoints are vulnerable to various attacks, including malware, phishing, and physical theft. To ensure the security of endpoints, protect devices from unauthorized access and maintain the integrity of encryption keys, the measures should be implemented:
- strict password policies or biometric authentication methods to unlock devices;
- keeping devices and software updated with the latest security patches;
- using secure communication protocols;
- strengthening physical access to devices through features like lock screens and encryption.
References
- Greenberg, Andy (2014-11-25). “Hacker Lexicon: What Is End-to-End Encryption?”. WIRED
- “Cryptography Concepts – Fundamentals – E3Kit | Virgil Security”. developer.virgilsecurity.com.
- Moldal, L.; Jorgensen, T. (11 February 2003). “End to end encryption in GSM, DECT and satellite networks using NSK200”. IEE Seminar Secure GSM and Beyond: End to End Security for Mobile Communications. Vol. 2003. IET. p. 5
- “End-to-end encryption.” Wikipedia, Wikimedia Foundation
- “Encryption.” National Cyber Security Centre
- Public-key cryptography – Wikipedia
- “Digital certificate.” Techopedia